A particularly effective phishing email is now circulating amongst Gmail users. It looks real enough that even tech-savvy individuals are falling victim to it. Security experts warn everyone to be on the lookout.
The people at Wordfence first sounded the alarm through a blog post.
How does this malware work?
As with any other phishing emails, this particular one attempts to trick you into giving up your email password. Once it has access to your emails, its developers can then take advantage of any important information in your inbox, including your passwords to other websites, private conversations, and other sensitive data.
This malicious email is highly effective that even careful users have been tricked. It poses as a normal email from one of your contacts. It usually comes with a PDF file attachment, which when clicked on will open to another page that looks very much like Gmail’s sign-in page. Except it isn’t a legitimate page but one that steals your private information.
Once the attackers got hold of your email, they can then use your account to send more malicious emails to your contacts, thereby widening the pool of victims.
Not only will your account be used to spread the phishing email to a wider network faster, once it is affected, there is a high chance that the attackers will corrupt other services tied to your email. They could, for example, execute a password reset for your bank accounts and other online subscriptions.
How can you protect yourself?
The usual advice of not opening emails from people you don’t know, unfortunately, does not apply here. This phishing hack effectively masquerades as an email from one of your friends or from a company you trust. What should ring an alarm in your head, though, is the fact that opening a PDF attachment should not open a new tab asking you to login to your email account, one that you have been logged into already.
Be aware, as well, that the phishing email that is currently making the rounds uses a technique called data URI combined with tricks to fool people’s perception. In the past, you may have noticed that if you visit a secure site, you will see the green lock icon or a green https://. For suspicious sites, you’ll see a red http with a strike through.
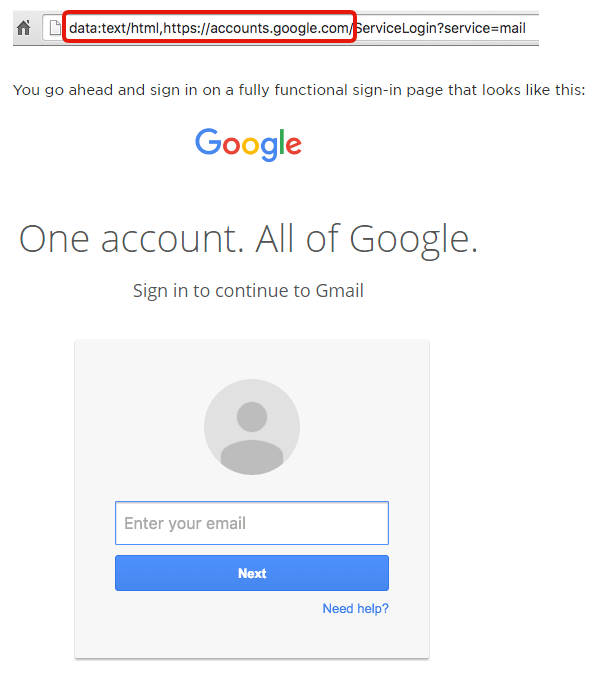
In the case of this malevolent email, the page that opens won’t have any different colors showing on the URL string. This tricks people into thinking that the page is normal and safe. But if you widen the address bar, you’ll discover that there are lots of white space between the seemingly normal URL string and a large group of text containing the program that facilitates the phishing.
If you did unwittingly open the email and click on the attachment, watch out for the new page that opens. If the Gmail sign-in page appears, check the address bar immediately. A legit URL should only start with “https://” and you should see the green lock icon on its left. If these are absent, or if you rather see other things like “data:text/html,https://”, then close that page immediately. That is the phishing portal hackers are using to acquire your private information.
Immediately delete the email containing the phishing attachment as well. And you might also want to inform the contact who sent the email to you that his or her account has been compromised. It is advisable to inform your friend via a different communication channel other than Gmail.
Continue keeping a close eye on your emails moving forward because this phishing hack is quite effective at the moment. Fending it off from one source will not guarantee your safety. Vigilance is key.
How will you know if your account has been compromised?
One thing you can do is check your login history. Go to the bottom part of your email list. On the lower right, you’ll find “Details”. Click on that to view your Gmail account’s activity history.
You will be able to check which browsers are accessing your email at what time and where. If you see any suspicious account logins, forcibly close them. Then, change your password right away. To be safe, also change the passwords of other accounts tied to your email. It is also advisable to report the matter to Google’s support center.
Moving forward, consider enabling two-factor authentication for added protection. For your other accounts, you might want to take advantage of a reliable password manager as well.
What is Google Doing about This?
Google recently released an official statement to Wordfence about the phishing attack.
According to Aaron Stein from Google Communications, they are “aware of this issue.” He further added, “We continue to strengthen our defenses against it. We help protect users from phishing attacks in a variety of ways, including: machine learning based detection of phishing messages, Safe Browsing warnings that notify users of dangerous links in emails and browsers, preventing suspicious account sign-ins, and more. Users can also activate two-step verification for additional account protection.”
When asked if Google is going to do something specific about a data URI type of phishing attack, Stein responded with “I can’t speak to things that aren’t out yet, but *please* watch this space. Should have more to share soon.”


