Technology over the years has grown more sophisticated and advanced. Information passes around at a much faster rate. If you are online, you are at risk. Trojans, viruses, spam, and other malicious software has been trumped by a more serious and harmful threat known as ransomware. It has been around for a decade and continues to spread far and wide.
The Nature of Ransomware


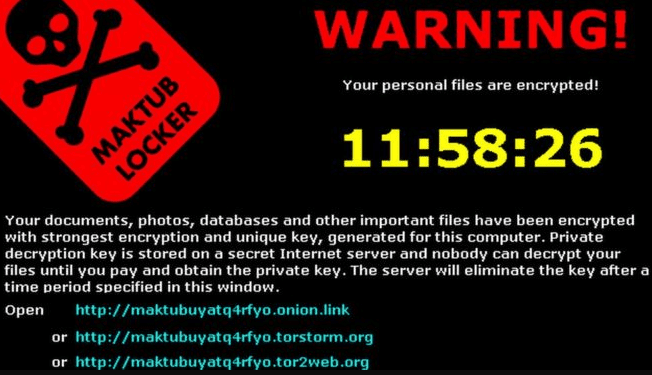
Ransomware is a subset of malware, which locks a person’s computer. It then scatters or encrypts files to render them unreadable or unusable, and will offer the owner a chance to decrypt if a fee or “ransom” is paid. The most common types of ransomware are encrypting and non-encrypting. In most cases, it threatens to publish or destroy the owner’s data to prompt a payment.
While other intrusive software attacks usually have their remedies, ransomware attacks are far more daring and cruel. Some malware may be slightly malicious and some may simply be annoying. Ransomware notifies its targets that they are under attack and charges a specific amount usually in bitcoin currency.
A typical ransomware infection occurs when the target gets exposed to emails that contain downloader trojans, or websites that will exploit browser vulnerabilities. Both will then attempt to install ransomware. Some models of ransomware are known as LockScreen (for Android), Cerber, WannaCry, Spora, and Enestedel.
Ransomware is considered a global problem. With many of its most recent attacks targeting big companies across Britain, Ukraine, Poland, and Russia. On the other hand, tracing perpetrators has proven to be difficult. This is due to most orchestrated attacks using cryptocurrencies. Bitcoin, for example, is highly used to receive the ransom. Since users are kept anonymous within the currency’s communication system, authorities find it hard to track them down.
The Rapid Evolution of Ransomware

Cybercriminal business models include ransomware-as-a-service (RaaS) and fraud-as-a-service (FaaS).
These and other types cyber-attacks have tripled over the course of a decade. They have significantly encouraged perpetrators to develop ransomware as a massive revenue source. In fact, criminals can create an extensive network of people who can be trained to launder money.
Cybercriminal culture has gone a long way. The capabilities of the software it constantly launches can automatically stay ahead of the cybersecurity industry. As specialist jobs are usually outsourced to the experts, cybercriminals or anyone wishing to become a perpetrator can start relatively complex operations. They can even do so without sophisticated gear or advanced technical experience.
The explosive growth of ransomware can be generally blamed on developers making cybercrime more accessible to anyone on the internet. Several malicious codes can be authored by these developers which can then be made available for download and use. Ransomware can also afford quicker payouts, which naturally entices other cybercriminals to convert. The end of 2016 observed a downward trend in ransomware attacks, but they started to pick up again by February 2017.
Combatting Attacks and the Ways to Avoid Falling Victim
If you are unfortunate enough to experience a ransomware attack, it’s best to refrain from paying the ransom asked. Paying will not guarantee a successful decryption of your data. Some perpetrators can only remotely adjust the state of the user’s files without restoring them.
In worse cases, paying the ransom can only make you more prone to receiving more attacks. Furthermore, you should also check the legitimacy of the ransomware by looking up its name, as some criminals can just twist some of the elements of an attack without actually installing the virus.
On the other hand, if you have recently paid with either bitcoin or credit card, then you must immediately contact your local authorities and your bank. There are also websites that may help you file fraud and scam reports. Moreover, knowing how to recognize scams can help you secure more of your data.
Protective Measures
Here are more preventive measures you should do to avoid a possible attack:
Make sure your desktop is equipped with reputable antivirus or antimalware software
Even the most basic ones can help you detect possible breaches, as most ransomware attacks are facilitated by getting exposed to infected links and attachments.
Always back up your files or data
Using an online backup service or simply an external hard drive can help eliminate threats. Tech professionals like Ori Eisen, founder of fraud prevention company 41st Parameter, recommends backing up data so you can always restore your system to default at any given time.
Always be cautious and on guard
Be careful with your digital footprint. It’s best to maintain an “assume breach” mindset, as recommended by tech experts. This can largely help you detect, respond, and recover from tampering. And can also ready you for future attacks.
Watch out for top ransomware names such as CTB-Locker, CryptoWall, and TorrentLocker
Small-scaled ransomware may be more common and active on the internet, but these ransomware families have been around for quite a long time. They are known to have combined fraud emails and exploitation kits posing as brands, victimizing people all around the world.
In the event of an attack, the first thing you should do is to disconnect your device from the internet. This will prevent infecting other nearby devices. Then seek advice or help from tech professionals who specialize in data recovery.


